intense Feed : See How to Prevent Brute Force Attacks.Mostly php Login WordPress Websites attack and how to defend it.
Since April 2013 ,WordPress wp-login.php brute force attacks increased. Brute frocing wordpress websites is really a powerful blackhat technique because it allows attacker to modify ,add ,delete or to do anything with website content after compromising username and password.A large botnet of around 90,000 compromised servers has been attempting to break into WordPress websites by continually trying to guess the username and password to get into the WordPress admin dashboard.
A ‘brute force’ login attack is a type of attack against a website to gain access to the site by guessing the username and password, over and over again. Other kinds of hacks rely on website vulnerabilities whereas a brute force attack is a simple hit and miss method and can be tried on any site.
How is a Brute Force Attack Launched Against a WordPress Site?
Brute forcing a wordpress website is easier relatively easier than any other kinds of attack. To launch a brute force attack on a site that logs into a user account, you just need to send the login form POST requests with the guessed username and password.
In case of WordPress, the POST request with the guessed username and password is made to wp-login.php file again and again.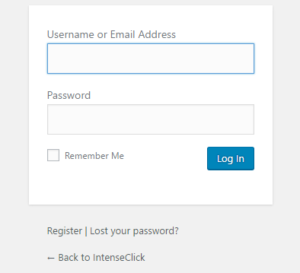
Now we will cover some methods that we can use to prevent brute force attacks against WordPress sites. WordPress is the most popular CMS and therefore it’s a frequent target of these type of attacks.
1. Verifying You Are Human | Prevent Brute Force
Most of the time, brute force attacks are made using bots. We can simply verify if a form has been submitted by a human or not. If it’s submitted by a bot then we simply don’t process it.
2. Use a Strong Password | Prevent Brute Force
Minimum password recommendations:
- Password should be consist of at least 8 characters.
- Add atleast 1 upper-case letter and 1 Numbers, punctuation or other non-alphanumeric characters.
- Dont use your name as password or mobile no.It’s probably a bad idea .
Example weak password: Alex1
Improved strong password: Z#hupsZ2M4!Z
3. Password Protecting wp-login.php
You can protect access to your wp-login.php file using HTTP Basic Authentication. This simply adds a extra security layer. Although a brute force attack can be launched against HTTP basic authentication but it’s difficult and time intensive to crack down both layers.
To password protect access to the wp-login.php file in Apache, follow the below steps:
- Generate a
.htpasswdfile using htpasswd generator. - Place this file in the same location as your
.htaccessfile. - Assuming your
.htpasswdfile includes the usernameintenseclick, place the code below in your.htaccessfile
## Stop Apache from serving .htpasswd files
<Files ~ "^\.ht"> Order allow,deny Deny from all </Files>
<Files wp-login.php>
AuthUserFile ~/.htpasswd
AuthName "Private access"
AuthType Basic
require user intenseclick
</Files>
4. Brute Force Login Protection Plugin | Prevent Brute Force
Brute Force Login Protection is a WordPress plugin which protects brute force login attempts by taking several factors into account.
This is how the plugin works:
- Limits the number of allowed login attempts for an IP Address.
- It allows you to manually block an IP address from logging into WordPress
- It delays execution after a failed login attempt to slow down the brute force attack. This can prevent the site being killed.
- It also informs the users about the number of login attempts remaining before getting blocked.
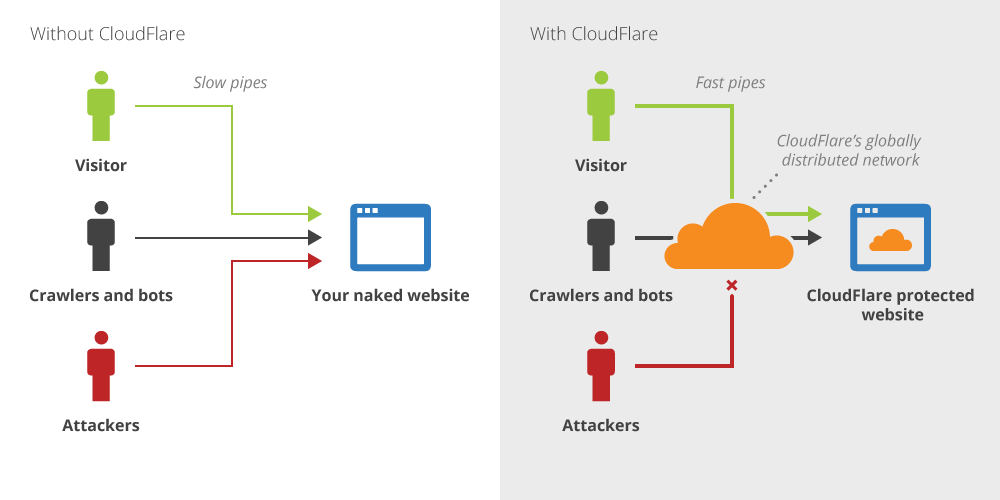
5. CloudFlare | Prevent Brute Force
CloudFlare is the perfect solution to prevent brute force attacks. Its has free and premium plans. Free plan is enough to get a decent amount of brute force protection. CloudFlare blocks every malicious or botnet activities ,before they even hit your server.
This image below shows how CloudFlare stops malicious requests:
6. Change default WordPress admin username | Prevent Brute Force
When installing WordPress by default the administrator user has the username of admin.
The botnet attack is currently only targeting this default username, so even having an administrator username of admin123 could signifiantly reduce the likilhood of your site being succesfully logged into by a malicious user.
7. Backup WordPress | Prevent Brute Force
Perform Backup of your whole website ,at least once in month(recommended once a week).It will help you to overcome from any Hacking disaster.If something goes bad ,then just restore your backup .that’s it
8. Make sure everything up-to-date | Prevent Brute Force:
As i always said ,Timely update will prevent Hacking .Updates are meant to be add extra features and security by developers.To protect yourself from any known exploits to WordPress you should update everything related to WordPress.whether its wordpress package update ,theme or plugin update.
9. Scan website for hacks, check Google Safe Browsing
If your WordPress site had been successfully compromised, a clear indication will usually be found either by a surface security scan of the website, or it will also get reported to Google’s Safe Browsing.
Scan your website with an online malware scanner like sitecheck.sucuri.net/scanner
Check Google’s safe browsing for your domain, at google.com/safebrowsing/diagnostic?site=example.com
10. Reasons to not rely Plugins :
There are many WordPress security plugins that attempt to automatically block such brute-force attacks. While these may work, I generally do not recommend them unless they provide significant other benefits.
Here’s why –
- The plugins still rely on PHP code. The protection is only as good as the code.
- The brute force attack still executes through the PHP layer. Under high rates of attack, this can cause load issues.
- Security in-depth. The likelihood of an exploit occurring simultaneously Apache’s authentication methods and in WordPress is low.
Conclusion | Prevent Brute Force :
You must be wondering which is the best solution? It really depends on which one you think is the best for your needs. For me personally, I use both CloudFlare and BruteProtect to stops brute force attacks on my site.
Let me know which one you think is the best solution for protecting against brute force attacks. Leave your thoughts and suggestions below.
Leave a Reply